After getting the virtual network set up, I was able to provide a contained environment for malware analysis. However, what happens when you want to study the behavior of malware that attempts to contact outside endpoints via the internet? Should you just allow it access to the internet? How can we know what/who it is trying to contact? The answer for this setup is utilizing a tool like iNetSim, which is a software suite that can simulate common internet services.
So, this takes some configuration in your VM’s (that you’ve already set up in an isolated virtual network). One VM should house iNetSim, which you can download here: https://www.inetsim.org/downloads.html. For every VM that you’d like to consider a “victim” to the malware as it runs, we need to configure which DNS server internet requests get directed to. For this example, I’ll be using a Windows XP VM.
To get to the DNS server configurations, in your victim Windows XP VM, navigate to Control Panel > Network and Internet Connections > Network Connections > right click on your Local Area Connection > Properties > double click Internet Protocol (TCP/IP). A window will pop up and look like this:
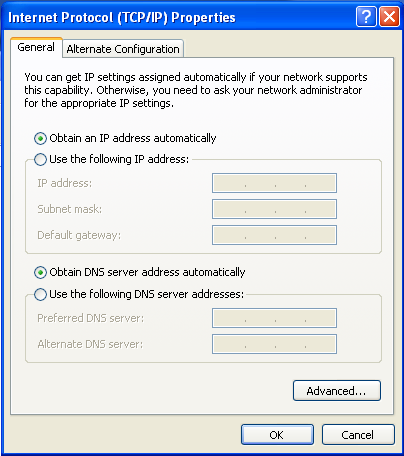
To configure the DNS server settings, select “Use the following IP address” and enter the IP address you want to use on the victim machine. I configured my virtual network subnet to be 10.1.2.0/32, and so the IP 10.1.2.100 is within this subnet. Add in the subnet mask, and then add the IP of the VM you are using iNetSim on (in this case 10.1.2.1) as the default gateway. Next, select “Use the following DNS server addresses”, and enter the same IP for the VM running iNetSim as the preferred DNS server. This will route all internet requests to the 10.1.2.1 IP address where iNetSim is listening. This prevents the malware from actually accessing the internet.
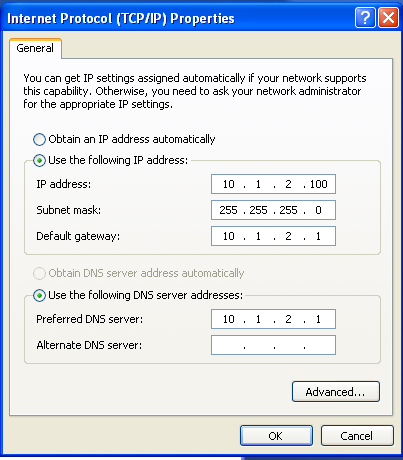
Now, let’s test it! First, let’s get iNetSim running on its VM:
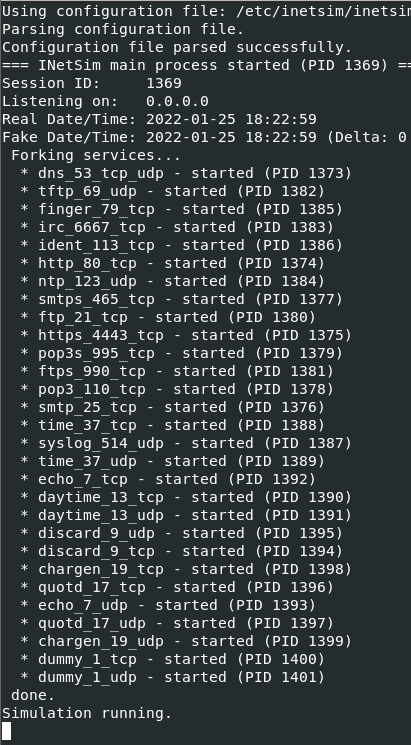
Then, let’s try to navigate to google.com from our Windows XP victim VM:
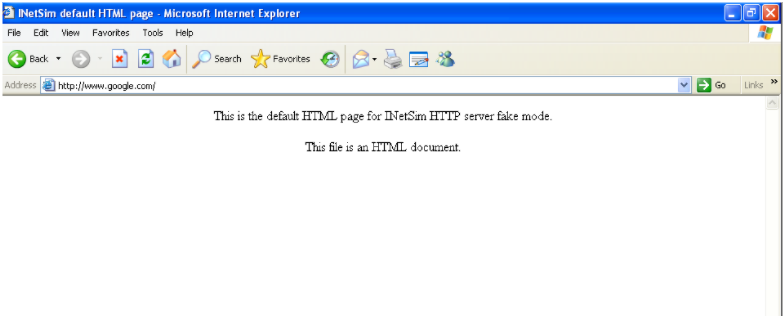
This redirects to a page set up by iNetSim as a default page. We can then stop iNetSim by entering Ctrl-C and open the log file that iNetSim wrote for each DNS query to a website:
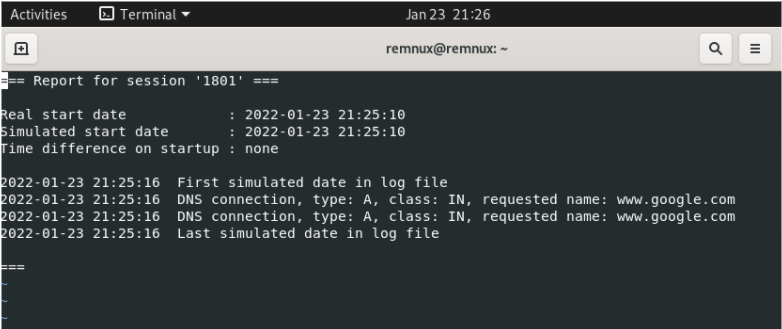
So we can see that there were two DNS queries for google.com! This means if we have a piece of malware that attempts to access the internet, we have a fake DNS server listening that our victim VM is configured to send these attempts to. We can then see and log each query for a site on the internet, gaining proof of the malware’s behavior!
References
Brian, “Adventures with inetsim,” Brian T. Carr, 04-Jan-2021. [Online]. Available: https://www.briancarr.org/post/adventures-with-inetsim. [Accessed: 25-Jan-2022].

