This week, we had their first two meetings with both of our project sponsors. A bit unexpected, but our project sponsor was a former student who completed the entire project last year. The project was intended to be taken down but was not. Long story short, my team will be recreating the same project from scratch! We will be modifying the project requirements slightly, but the main concept will still be the same. Since the project sponsor was a former student who was not expecting to be a sponsor, we will be working partly with the student and partly with our instructor throughout the year. The good news is we have more flexibility in what we create. The bad news is, we have to start completely from scratch. Now, we must also come up with a new name for our project. Hence the title of this blog post, Name TBD.
First Impressions
Our first meeting was with the former student who initially proposed the project. Thankfully, they were kind enough to assist us in developing project requirements and even offered to help us if we got seriously stuck. They gave us beneficial advice about using trusted cryptography libraries, so we do not have to reinvent the wheel. Our sponsor also gave us advice on a specific framework for .NET and WebAssembly which they used in the project. The framework is Blazor. This framework is intriguing because it enables us to use mostly C# for web development. With traditional web design, the languages used are mostly HTML, CSS, and Javascript . While there will still be a need to use some of the traditional web design tools, using a framework like Blazor will give us increased flexibility which will allow us to spend more time learning the C# language and the .NET framework.
Second Impressions
Out next meeting was with our professor, Bill Pfeil. We went over the project requirements and stretch goals. Which as of now, are:
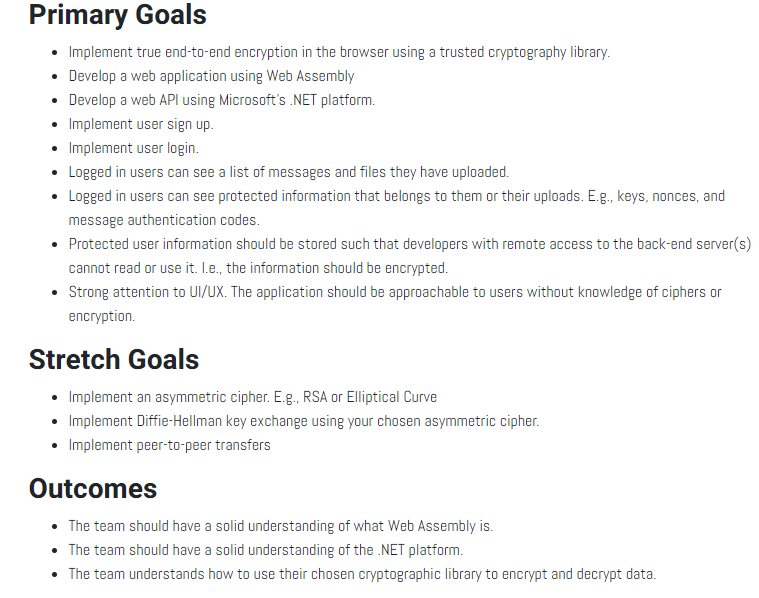
Bill gave us solid feedback on the project scope and encouraged us to accomplish the stretch goal peer-to-peer transfers. Overall, he though this was a great project choice for a senior project. My teammates and I have some background in security which makes us ideal candidates for this project. As it stands, it appears I have taken the most security classes, being the only one who’s taken Cryptography, Defense against the Dark Arts and Intro to Security at Oregon State. I am excited to apply some of the theoretical knowledge I learned in the Cryptography course into this project. Specifically the stretch goal of implementing Diffie-Hellman key exchange.
Next Steps
The next steps I’m hoping to accomplish with my team is to start developing a UML-like diagram to outline the different components of our project. Since most of us have not worked on a project with this big of scale, I believe understanding how different components of our software will interact with each other will be critical in maintaining good development speed. We also need to further define our project requirements down to the small details and start thinking about other questions we have. I’m hoping we can start development sometime around the end of winter term. If we can get an adequate development plan in place, we may even be able to begin work during winter break!



