It’s getting into the thick of the term now and things are getting busy. As of now I’m trying to balance being a new dad/husband, increased responsibilities during the 45 hour work week, and increased workload from the 11 credits I’m taking. I’ve been in school now a combination of part time and full time for 7 years, this is my 8th. I’m extremely excited about graduating and I’m optimistic about how my work experience, combined with my experience at OSU can help further my career. I dream of the day where I only have to work and don’t have to take classes anymore. While I have enjoyed my CS classes throughout my education, I’m ready to start coding more at work, and less in my hours outside of work. Even though life is busy, work has been very exciting recently!
Automating My Job
Right now there are not a lot of new developments with my senior project. So it seems like an opportune time to discuss some of the exciting things I have been doing during my day job. I currently am a service desk technician, but my workplace has been very receptive to improving processes using scripting, or any other method I come up with. I started learning some PowerShell in my spare time at work, and I found that it’s basically a programming language. To me, it really codes codes like a combination of Python and C++, two languages I’m very familiar with. I knew that it was a scripting language but I did not understand it’s capability to make such advanced programs/scripts.
Using PowerShell has been exhilarating and inspiring so far. I was able to take an existing script that was probably 300-400 lines of code used to create ActiveDirectory users that my organization had, and improve on it drastically. The project is now north of 4000 lines of code and automates essentially the entire user creation process for Active Directory. Office365, and AzureAD. I was able to use a PowerShell Module to import data that defines what permissions and licenses users get. The script I created uses some of my knowledge of control flow, data validation, and advanced data structures like nested hashes. This has been a fantastic project that I will certainly bring up when interviewing for future jobs.
Gitting better with Git
The PowerShell Script I wrote for work was a huge learning experience. It was the first time I had ever worked on such a large project. It was especially challenging because not only was I learning PowerShell and learning some of the oddities with ActiveDirectory, but I was also learning how to better use source control and trying to utilize Project Management Software as best I could.
I had done some of these things in classes, but for me, until you do it in the real world with a project where source control actually makes sense, it’s difficult to really learn how to use it best. I reached out to some friends and did some research on best practices and I know I’ve come a long way with using source control. I finally see the value of source control for real, it has saved me several times when I have accidentally made a mistake. My favorite method of using source control so far is to use a structure similar to this:
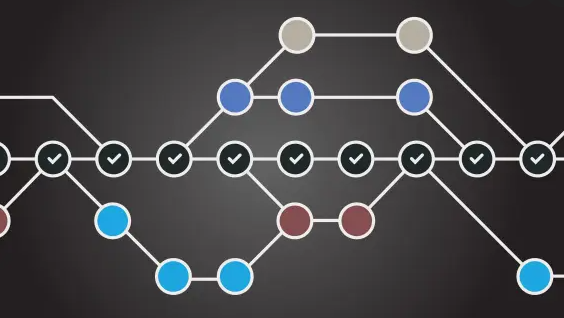
In this diagram, the black center line is the main branch that contains the working version of the code and the colored lines are different branches. Whenever I want a new feature implemented, I create a copy of the working branch, develop on it with multiple commits. When a branch/feature is completed, I merge it into the main branch. If I’m working on another branch that was copied at the time before the most current merge, it’s simple enough to just pull the changes from my most recent commit and my active branch will update. This makes it easy to separate different features and implement them into the main branch when I want to.
I’ve also learned how to use tags and versioning. Tags have been been useful for when I reach a “checkpoint” in my code. They allow me to easily define certain features that I’ve implemented, and allow me to keep a script version. With each version having a certain amount of changes. The most beneficial thing I’ve learned here is how to properly version software, and how to write patch notes and how to best communicate that to the team that will use them.
Updates on TransferMe
The experience I’ve had from work building a large PowerShell script makes me excited for the time where I can work on a large scale project with my 2 teammates. We are going to be setting up our development environment soon, adding notes to our Trello board, and getting our GitHub repository set up. I did some more research on the cryptography side. My teammates have been researching the website design and the database design. It will be exciting to work together to build a large scale project that we can all be proud of!